INTRODUCTION
On 12 June 2022, iitk.ac.in, the main website of our institute was hacked into. The words: “ALL YOUR DATA HAS BEEN DELETED FROM YOUR SERVER” were flashed on the screen.
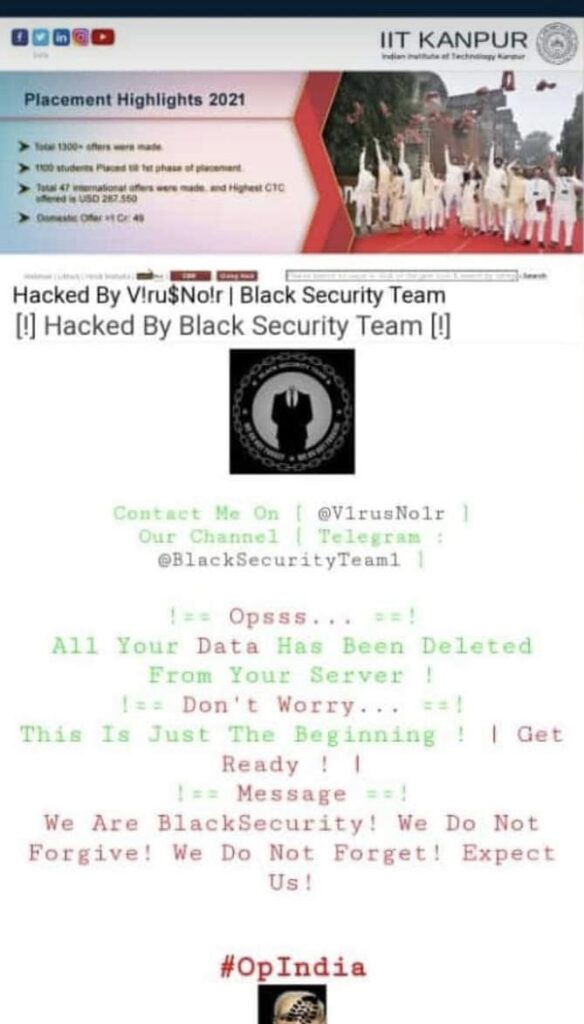
Many people might consider this as just a wrinkle, but delving deeper into this, we came across a lot of questions. First, are other IITK websites vulnerable as well? Our campus is home to over ten thousand people and consequently, any vulnerability in such a huge network infrastructure that powers it, has significant consequences. Second, an enormous amount of personal data including our name, contact numbers, family income and address is stored on Institute websites like Pingala, OAG and HelloIITK. How safe is our personal data? Third, is the framework of our institute strong enough to protect us against malware and data leaks, and if not, what else can we do as users to protect ourselves?
To answer these questions, we contacted a number of students who have exploited these vulnerabilities and professors responsible for handling cyber security issues. Here are our findings:
PROBLEM 1 – SPAM EMAILS AND LINKS
According to Prof. Sandeep Shukla, many campus residents do not use any anti-virus software when connecting to the internet and hence, their computers remain susceptible to malware. We came across an incident where a Ph.D. student lost all her work because she was using pirated software without scanning it for viruses. We have also seen system attacks because the user clicked on seemingly harmless links. Ransomware attacks, (attacks in which an external body attacks websites, servers, desktops, laptops, or even mobile phones and holds it hostage till a particular sum is paid as ransom), is another serious challenge for academic institutions. Years of cutting-edge research, stored on institute computers, can be taken hostage by such attacks. Unfortunately, IITK does not have a policy to deal with ransomware attacks.
Moreover, IITK webmail only uses rule-based filtering to filter spam emails. The license for these rule-based filtering systems is bought by the Computer Center and contains institute-specific rules to filter out spam emails. However, such spam filters are much inferior to ML-based filtering algorithms used by commercial email providers like GMail. When asked why IITK cannot move to GMail or other commercial email providers for its email service, Prof. Manindra Agrawal said that all Government departments have been restricted from storing data on foreign servers.
The onus, therefore, falls on the end user. Prof. Manindra Agarwal added, “it is absolutely important that everyone on campus is aware. People still keep falling for Nigerian princesses, which is surprising in a technological institute.”
PROBLEM 2 – LACK OF UNIFORMITY
Our institute network consists of several web pages hosted by various professors, administration, research groups and students. Some of these websites are dynamic, whereas others have not been updated for a very long time. Dynamic websites offer more functionality but are also more vulnerable than static websites. Most institutions abroad have a template for web pages that can be hosted on their network, but IITK, like most Indian Institutes, does not have one. Prof. Sandeep Shukla stated that “the CC has always chosen functionality over security. This lack of a uniform website template makes the IITK network further susceptible.” Post the incident on 12 June (the hacking of the IITK website), the institute decided to allow web sites and web applications to be ‘created only after approval from concerned authorities.’
PROBLEM 3 – SIMPLER VULNERABILITIES
Prof. Sandeep Shukla told us that earlier Pingala gave the user unlimited attempts to guess the OTP when changing their password. Hence, a simple python script could be used to reset the password of any user.
Not just Pingala, but OARS and HelloIITK are also plagued by several vulnerabilities. A student has demonstrated that it is possible to hack into a certain website and get access to the grades of any course, by running just a few commands. An alumnus told us that a glitch in HelloIITK allowed people to access the PDF of a question paper before it was made publicly available by manipulating the URL. Fortunately, all of these loopholes have now been fixed and are stated here as an example. But several other vulnerabilities still remain open for attackers to exploit the IITK network.
An alumnus who hacked into Pingala, stated that the administration, on his request, asked the people in charge of Pingala to take appropriate measures, but little has been done in that direction.
THE DEFENSE MECHANISM
All this leads one to wonder how secure all the data in the institute is. According to Prof. Sandeep Shukla, like most other institutes in the country, IITK does not have a data security policy to deal with cyber attacks.
A committee was formed 6 months ago, when a fellow professor was able to hack into 2 administrators’ websites, stated Prof. Shukla. However, he added, that the committee has met only once since then, and that security is not being taken seriously in our institute.
When asked if there is a need for data consent forms in the institute, Prof Manindra Agarwal stated that “consent is assumed to be implicit”. Some foreign institutes are known to have a consent policy in place, however in India, it is assumed to be implicit. The institute has no reason to sell your data to third parties, but with all the vulnerabilities which exist, this might be a good time to look at steps that are being taken to mitigate them.
The C3i lab, headed by Prof. Sandeep Shukla and Prof. Manindra Agarwal, has framed data security frameworks for large organizations such as NHAI and helped them establish a data ownership/security policy.
Prof. Manindra Agarwal stated that they plan to propose the usage of C3i systems for the institute cyber security. It is impossible to monitor all the accounts and emails and 1000s of data bits, and C3i would make life a lot easier for CC engineers.
WHAT CAN WE DO?
There are some personal responsibilities that should be taken care of by the student community and the faculty as well. This includes simple habits such as changing the passwords regularly, avoiding keeping common passwords for multiple sites, and avoiding writing passwords down, (rather, write hints for the passwords if you have a fear of forgetting the passwords).
Prof. Sandeep Shukla also suggested that students should always log out of their accounts and remove the details on public devices. One should clear the cache and history if not working on their personal devices. He also suggested that people should not make monetary transactions on public wifi.
In addition to this, Ashish Dutta, the current DDIA of IITK has been sending out emails to the students about how many students fall prey to bad internet practices and end up revealing their passwords to miscreants on the internet. These accounts end up being used to spam the institute. He also mentions preventive measures in his mail, such as changing your passwords and being wary of external links. It seems that there is still a lack of awareness among students about potential security threats on the internet.
In conclusion, we believe that the institute must continue its efforts in creating a robust framework in which such security hazards are eliminated. At the same time, there is a need for users to be much more aware and careful about cyber-security hazards.


Written by: Aditya Mishra, Aviral Upadhyay, Chinmay Pratap, Khush Khandelwal, Rahul Jha, Ridin Datta, Shreya Nair, Talin Gupta
Photo Credits: Atharv Jiwane
Edited by: Sanika Gumaste











